President Donald Trump recently reiterated a pledge to build a team that will provide him, in his administration’s first 90 days, with a plan to “aggressively combat and stop” cyberattacks.
Topping the list of the new administration’s priorities should be the need to articulate a comprehensive strategy of cyber deterrence.
In outlining policies to shape a deterrence posture, this team would be doing a disservice to the president and America’s cybersecurity if its recommendations did not include support for private sector active defense against cyber threats.
By supporting capable businesses seeking to take proactive steps to defend their assets in cyberspace, the new administration can secure a cost-effective policy win with significant potential to improve whole-of-nation cybersecurity.
The surge in public debate surrounding cybersecurity policy in recent years is indicative of the fact that cyber threats are growing in scope, size, and systemic importance. This problem is compounded by the fact that common responses to cyber aggression are outdated, reactive, and insufficient.
To reverse these troubling trends, America’s cybersecurity strategies and capabilities must begin to match the conditions of the next decade better than they match those of the previous decade.
The Trump administration’s cybersecurity strategy must be grounded in the fact that merely upholding the status quo is a recipe for failure. The president must break the cycle of policymakers who seem to merely admire the problem and then expect different outcomes to come from the same tired policy responses to malicious cyber operations.
Utilizing the Private Sector
America needs to be sensible yet bold in its efforts to deter cyber aggression. One realm of strategic significance that is ripe for such action is private sector cybersecurity.
The Trump administration should capitalize on the industry’s resources, expertise, and position on the front lines of cyber conflict by supporting the responsible expansion and normalization of private sector active defense against cyber threats.
Recognizing the potential for meaningful progress through nonincremental policy changes related to private sector cybersecurity, the Center for Cyber and Homeland Security at the George Washington University recently released a detailed report on the legal, policy, and technology considerations relevant to active defense in the private sector.
Its recommendations to the executive branch include the development of public-private coordination mechanisms, continued clarification and socialization of legal enforcement guidelines, and the prioritization of funds for research and development related to active defense measures.
However, some of the report’s most fundamental contributions to the pursuit of sound cybersecurity policy are its efforts to assess the varied usage of the term “active defense,” to propose a common framework for considering private sector active defense going forward, and to call for greater clarity from government actors on how they approach related issues through legal and regulatory lenses.
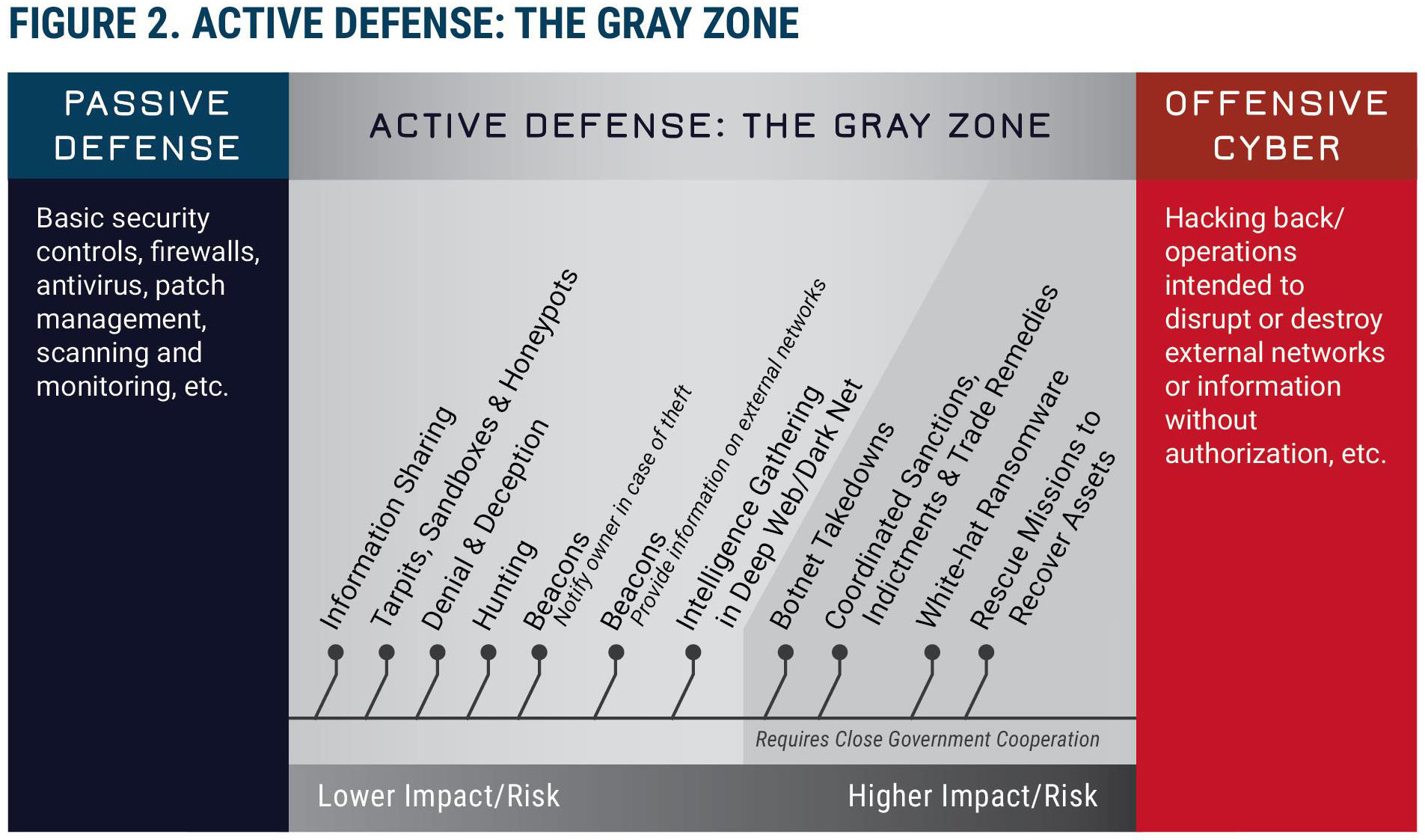
The term “active defense” refers to a spectrum of cybersecurity measures that range in relative impact and risk and fall between activities that are commonly described as passive defense and offensive cyber.
This graphic from the Center for Cyber and Homeland Security report illustrates the concept of such a spectrum and indicates the relative positions on this spectrum of some of the most common active defense measures.
In order to promote effective policy dialogue on matters related to private sector active defense, it is important to explore in greater detail some of the measures that are included in the active defense toolkit and how they should be used by private entities.
Legal Obstacles
The lower-risk active defense techniques, those that take place wholly within a defender’s network, such as the use of honeypots and hunting techniques, are clearly legal under current statutes.
Honeypots lure hackers into isolated areas of a network that allow defenders to safely gather intelligence on an aggressor. Hunting refers to procedures and technical measures that detect and then remove intruders from a network.
Many companies already use these techniques to supplement passive defenses.
Moving up the scale of relative impact and risk, there are measures that should be legal for private actors, but are shrouded in ambiguity because they involve actions that can take place outside of a defender’s network.
Beaconing, which tracks stolen data outside of a network, is one example of an active defense activity that many businesses avoid out of aversion to potential legal risks, despite their capacity to improve cybersecurity and attribution.
Determining the legality of a cybersecurity measure based solely on whether it takes place inside or outside of a network is often inappropriate and should not preclude the use of sound active defenses.
Finally, the riskiest active defense techniques should only be legal for private businesses if they are operationalizing such techniques in close cooperation with a government entity.
Botnet takedowns and the use of software that locks stolen files on a third party’s compromised system before the stolen information can reach the malicious actor (white-hat ransomware) are examples of such activities.
These examples, details, and contextual considerations related to active defense measures are key to facilitating the discussions needed to explain why it is imperative that the new administration works to expand the latitude for private sector cybersecurity.
Private businesses never anticipated that they would be forced to defend their operations from adversaries as capable as the foreign intelligence services of nation-states. Yet that is what they are forced to do in cyberspace.
Unlike more traditional threats, cyber threats are so decentralized and numerous that the American government does not have the resources or bandwidth to be the sole provider of security in this realm.
The legal and reputational constraints on the private sector’s ability to aggressively and proactively defend itself thus creates a gap in the nation’s cyber armor that exposes the integrity of private sector networks and data. If malicious actors were to take full advantage of this cybersecurity Achilles heel, such actions would seriously threaten national security, the economy, and privacy.
A Worthwhile Partnership
The private sector needs better government partners going forward. Regulators and support agencies should quit blaming the victims of cyber exploitation and instead work with businesses to raise the costs on cyber criminals and adversaries.
This shift can begin with joint public and private efforts to build private sector capacity for active defense. By jointly developing and marshaling cybersecurity capabilities, public and private sector actors can move beyond the pablum and flip the equation of cyber conflict so that deterrence becomes possible.
The president and his team of cybersecurity experts will inevitably face several challenges while developing a cybersecurity strategy and defending the nation against malicious cyber activities during the coming years.
Supporting private sector active defense in rhetoric and policy is akin to victory in an early, decisive battle that will significantly improve the cybersecurity of the private sector and the broader security of the nation.